How does a framework work?
Wikipedia says framework is …
“A framework in software development, is an abstraction that joins common codes among various software projects providing a generic functionality.“
By analogy, I can suggest the operation similar to that of a wrench, as it is something that facilitates and streamlines the way of development with many utilities ready and pre configured.
They all have standards, such as folder structure, files. This frameworks are organized to separate file types by responsibilities, such as view, controller and model if it is a framework that uses an MVC standard and also separates files according to their extensions such as static js, css, html files, as configuration files of system that can be an ini, yaml, yml, xml, cache files and logs among others.
In this article we will talk about the main ones.
- Laravel
- Zend
- Symfony
- Codeigniter
- Yii
- Kohana
The problem?
The problem happens when the framework is not implemented correctly, as it guides the documentation. It is worth emphasizing at this point, that this is not a failure of the frameworks, but of implementation. Of course, there could be changes in the framework that would help to mitigate the security problem.
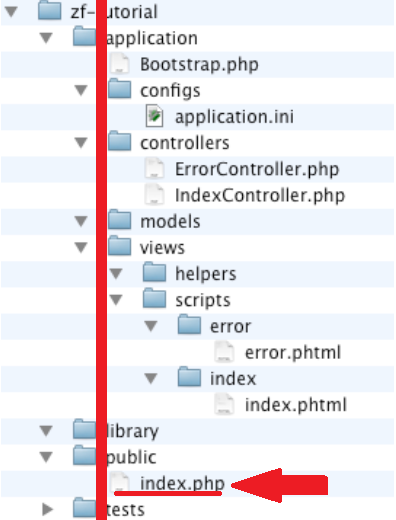
Every framework has a folder where it is to be pointed to the main url, usually an index file in a folder called “public”.
Por exemplo:
For example:
The site https://www.example.com/ is pointed to folder on the server /var/html/example/public/ (remembering that the hosting services give access from the system user’s folder in this case /var/html/example/) and you can not return folders because public is a final level, only with static file folders usually.
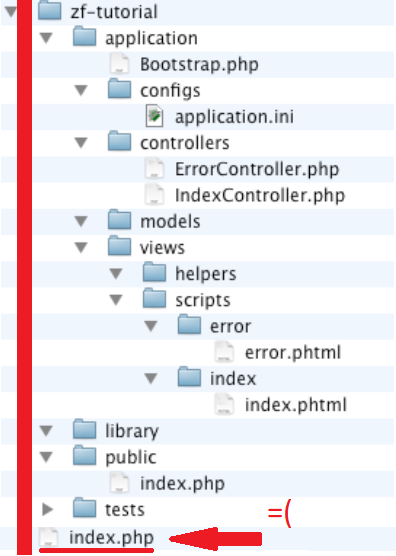
The problem happens when you point the home page to a folder that is earlier than the public folder. For example /var/html/example/.
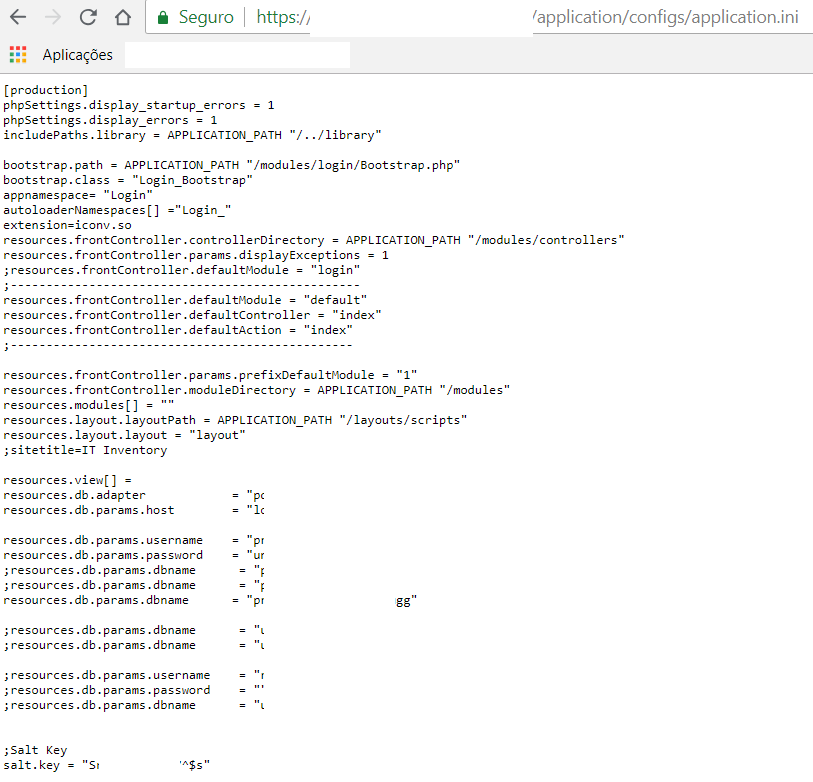
The first problem when you point to a previous folder is that on the same line as the file structure you have other system folders in addition to the configuration files. You can navigate through the url, for example https://www.example.com/application/config/.
The second problem happens most of the non-system configuration files (at this point I think the frames could have helped in the security part), are files that if found in a common url like https://www.example.com/application/config/apllication.ini and will be printed on the screen.
Another common problem, are to insert multiple systems just by inserting into folders after the main page.
For example:
We have the home page, https://www.example.com/ that is using some framework and is configured correctly. But it has a list of systems on the same server more on the front legs of the main.
- https://www.example.com/system/frameZendSystem/application/config/apllication.ini
- https://www.example.com/system/frameLaravelSystem/.env
- https://www.example.com/system/frameSymfonySystem/apps/backend/config/parameters.yml
How to exploiting?
What we are going to try to do is to find open system sensitive files, since it is possible to extract data such as host user and password from the database or stmp data, as well as other sensitive data such as logs and caches.
Targeted attack:
Locate folders without the index.php or index.html to return the listing of files and folder. Through this action we can analyze the patterns of folders and files to identify the framework. After identifying the framework and the version between paws and checking files, the second step is to go to the folders that have sensitive files, or open them directly..
Large-scale attack:
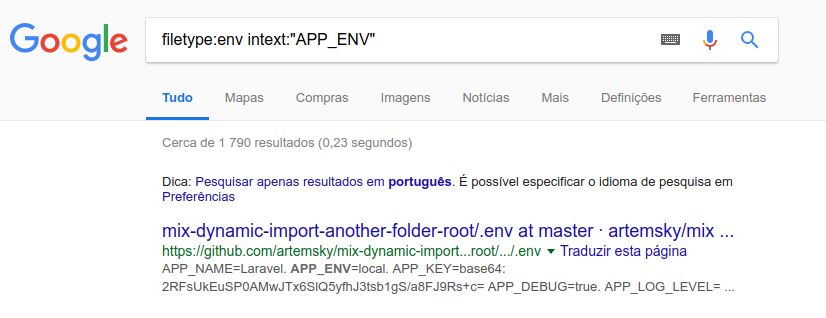
Through search sites like google, bing among others is used dorks 1*specific to each framework, we can list thousands of systems with configuration problems and exposed sensitive data.
Examples:
Clique to Continue Part 2
See in the second part of the article.
1*- Dorks: A Google dork is an employee who unknowingly exposes sensitive corporate information on the Internet. The word dork is slang for a slow-witted or in-ept person. Read More…
Obs: Article write by me with contribution by Subsolo Vinícius