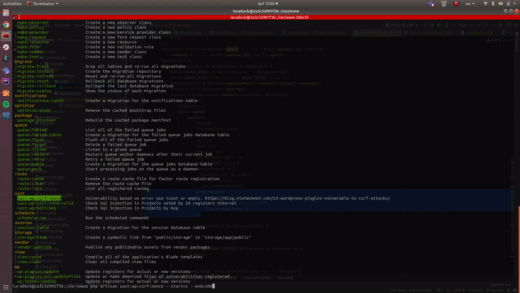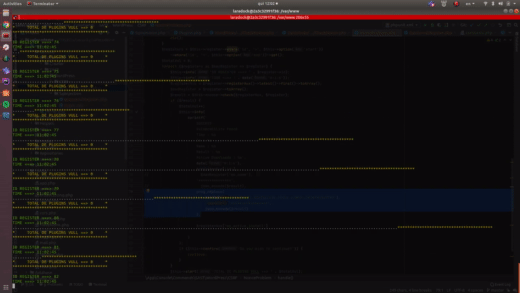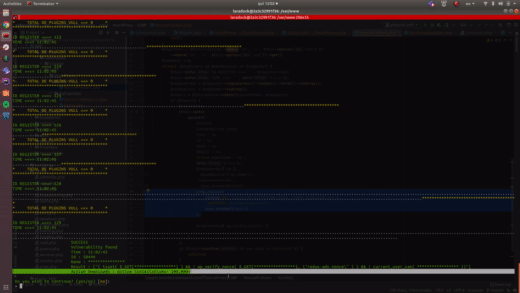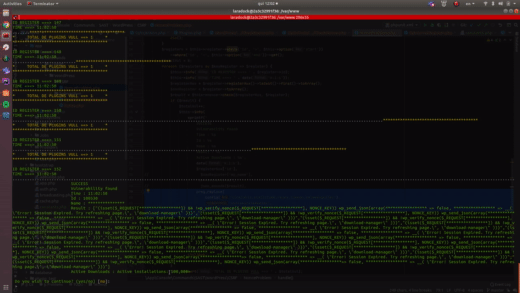
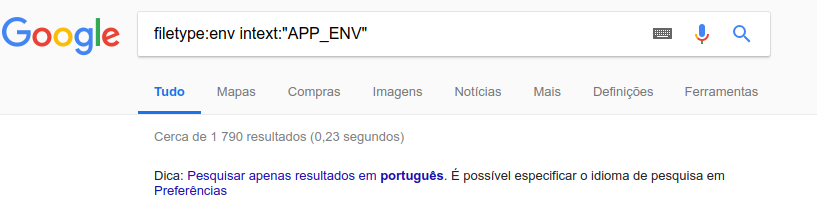
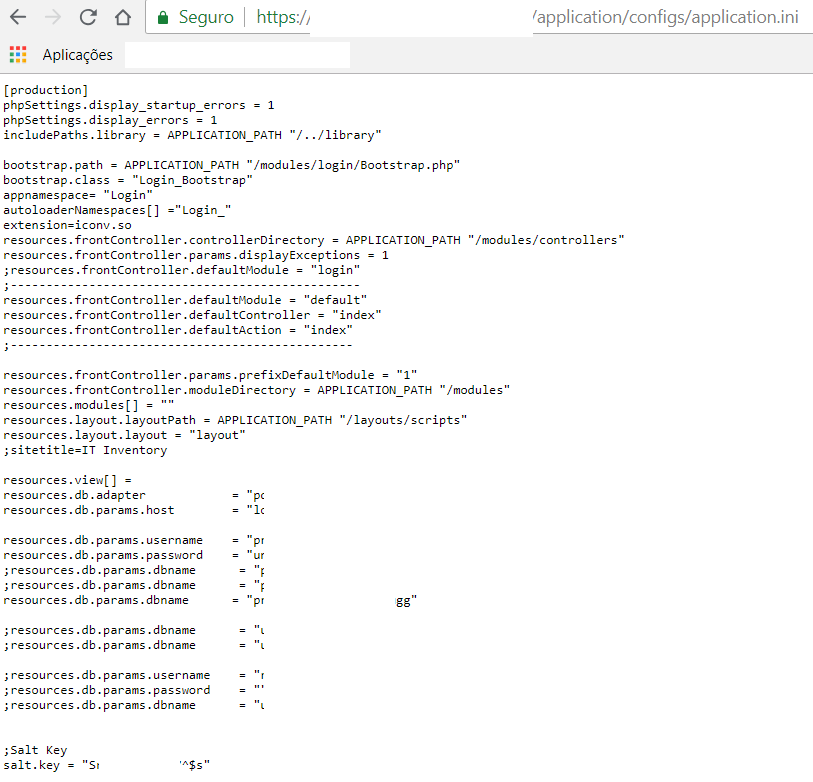
Exploiting vulnerability in logical operators “isset (…) && !Anything”
Look this code: if ( isset( $_POST[‘cartflows-action-nonce’] ) && ! wp_verify_nonce( sanitize_text_field( wp_unslash( $_POST[‘cartflows-action-nonce’] ) ), ‘cartflows-action-nonce’ ) ) { return; } This code was taken from a WordPress plugin with more than 100,000 active downloads, Cartflows (https://wordpress.org/plugins/cartflows/). This condition is a security validation to block CSRF, it works to …