This is a first post written in English and probably have a grammatical error but talk to me and I set.
Obeservation:
This article will show two sides of the coin. One side, teatching the badness (using a tool that is in my github), other side, teach how we can mitigate the risks.
Introduction:
I am a fanatic about security and development and a desesperate friend asked to help me for indentify and cleaned the site that was full of malwares. He said that had been invaded sometime, and before things he tried, the problens ever returned. He believed that was maked sometime things wrong. I was analyzing because that was happening.
First time I identified many malwares and with many types and with difference dates, but the important was a folder that was listing many files with reference the sensibles files database or configuration of others users. So I realized that the site was serving of hub for others sites. Identified the file that execute this procedure and maked a reverser enginier for undestand how the site served for atack other sites.
Environment:
initially the site was a cms, WordPress updated, with few plugins and organized. The Service was a retail server, shared ohters sites/system of others users. But for the validation and comprovation, the similar procedure was make in other 6 servers, all shared servers too. This servers contain of 4 at 600 system/users by servers.
Fact:
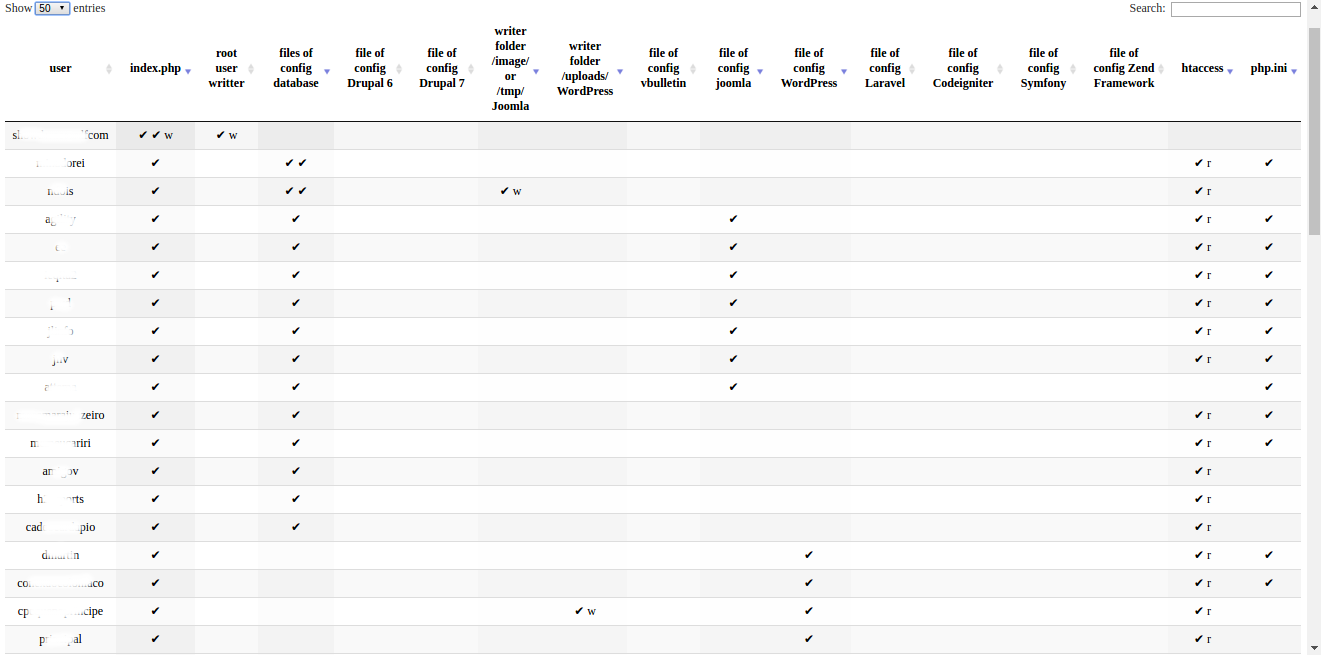
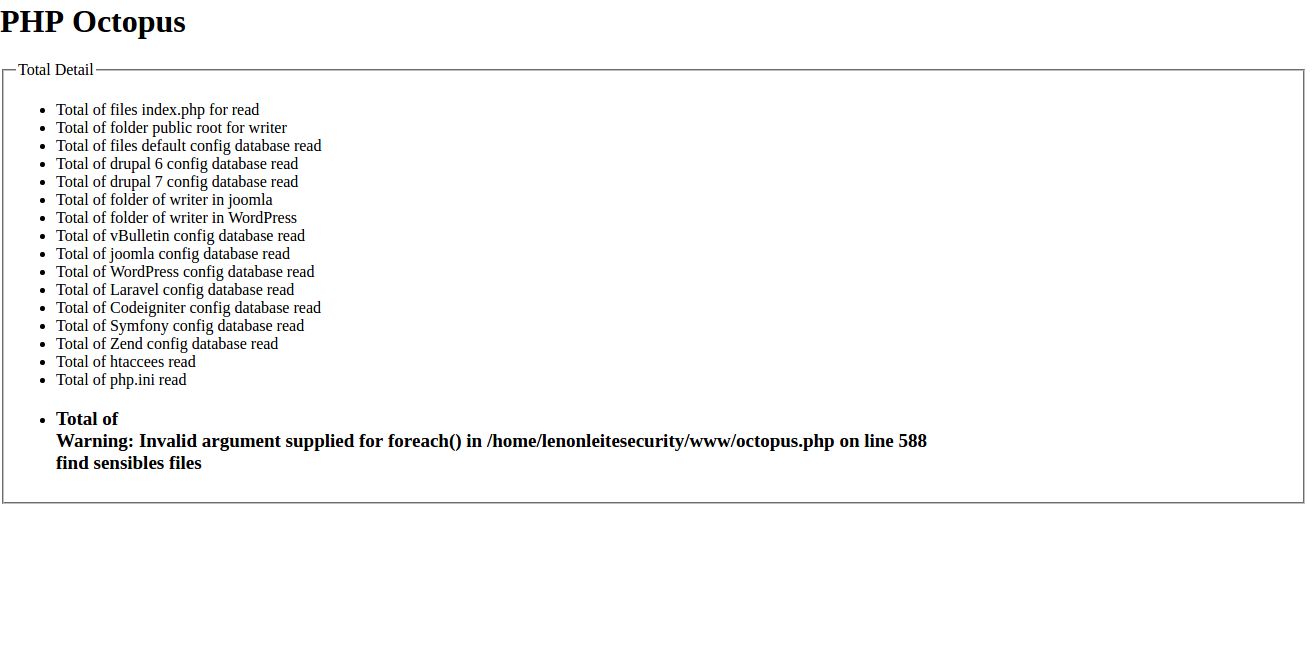
After to estudy and analiser the malware, I modification in how checked and created files used symbol links for ready only and pontencialized the results in 3x or 4x more results, as well many others extractions of information with writeable folders and parten system with cms and the most widely used frameworks. So borned the “php octopus”. A little file that work how a octopus with its tentacles scan all server for find files of configuration.
But how?!
- All system linux has a file with name passwd that is in the folder / etc /. This file is salve all users of server, this file is the key of all, but exist other alternatives for find users but less eficient.
- I check if the actual folder has a structure / home / my_user / public_html / , for default in servers linux.
- I do the read of file passwb and list all users for a loop.
-
Next step, we will search configuration files, files of database, system or writting folders. Exemplo:
-
- All site init with index.html or index.php in php, last item is that important for us, so checked if existe this file / home / my_user / public_html / index.php
- In case of WordPress site used / home / my_user / public_html / wp-config.php
- In case of Joomla site used / home / my_user / public_html / configuration.php
- And many others standards indentified how cms and frameworks
- And in the end return data of files and os information if folder is can write or not.
Solution:
Many peoples will say that the problem is permission wrong. Correctly, but what? All system have folders with permission 755 and files 644. Where is wrong?
The result is:
- Server:
- Eliminate view of file / etc / passwd for common users.
- Eliminate access of users in folder of other users, for view or writting.
- Usuário:
- Edit permission of root folder for 750.
- Never use 777 for folders or files.
- For statemant, internal folders use 755 and files 644. Only internals, this root folder 750.
How do you do for test:
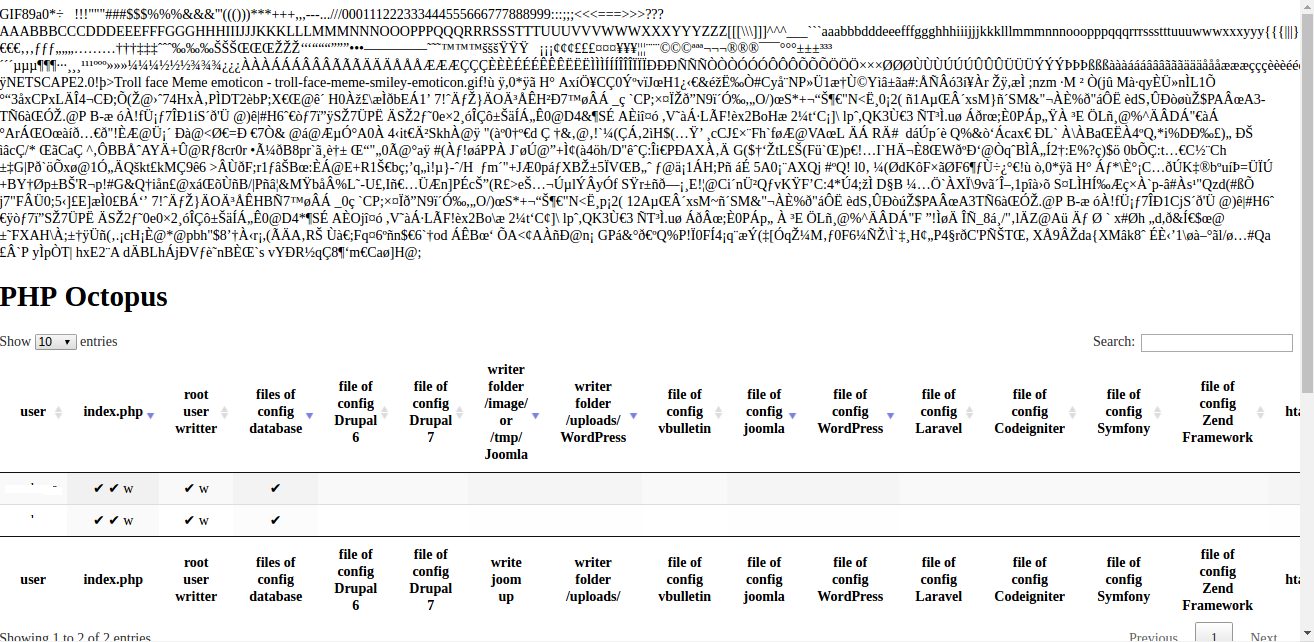
Make download of file octopus in https://github.com/lenonleite/octopus and insert in your server. Existe two files, a simple file and other with stegonography with header metatag in gif for by pass in system of upload if necessary.
See the vídeo:
Server 5:
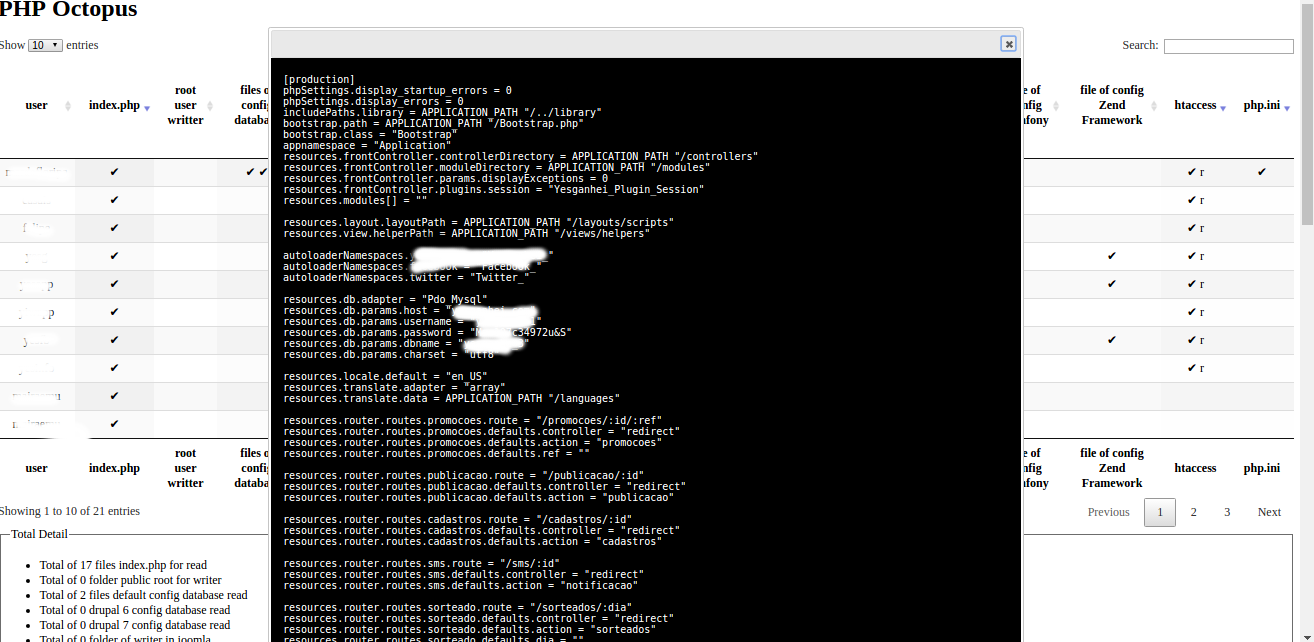
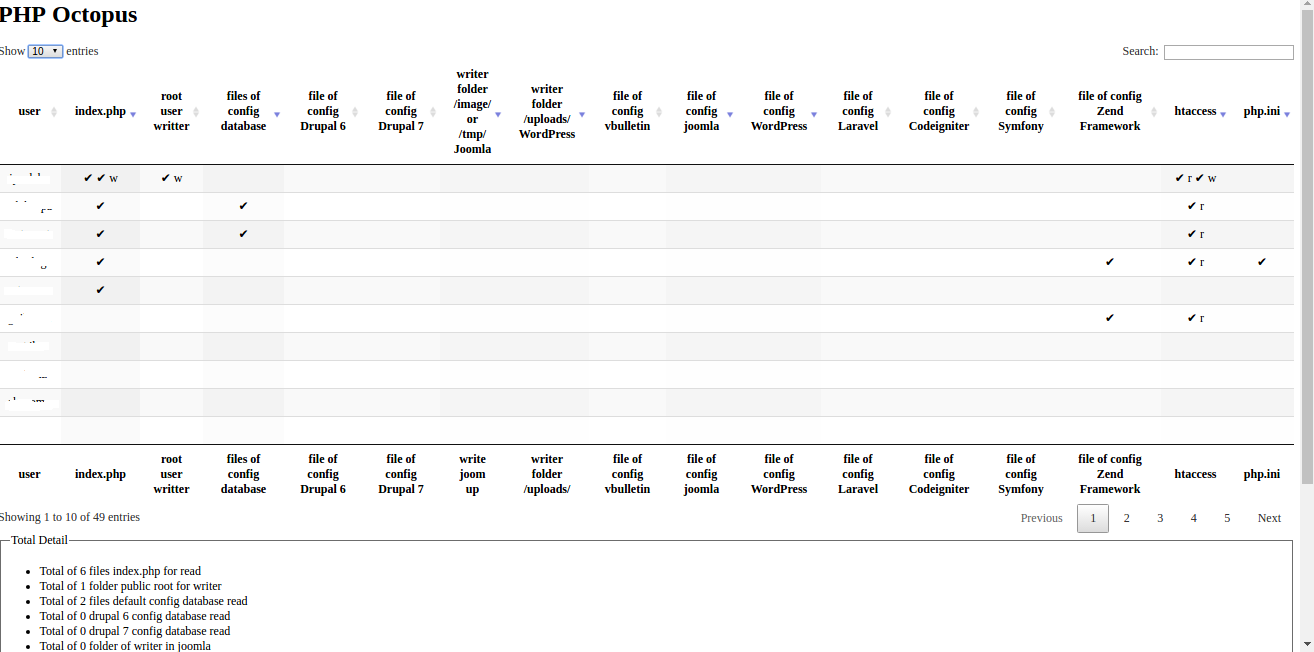
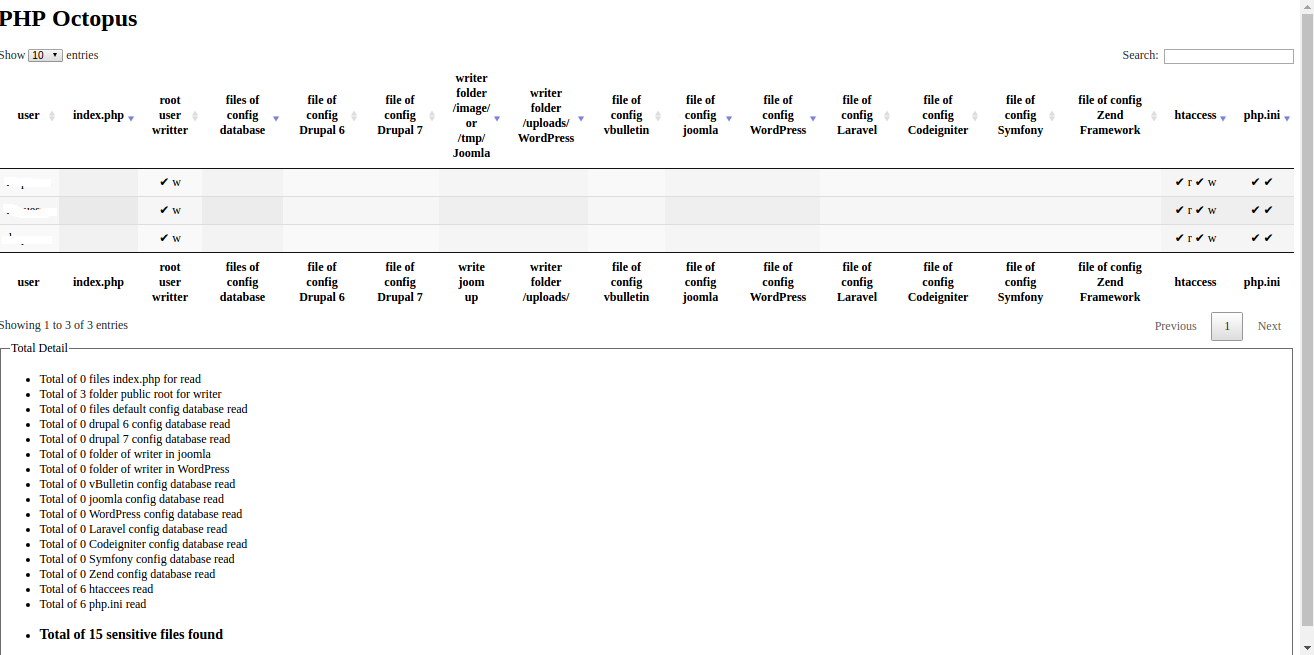
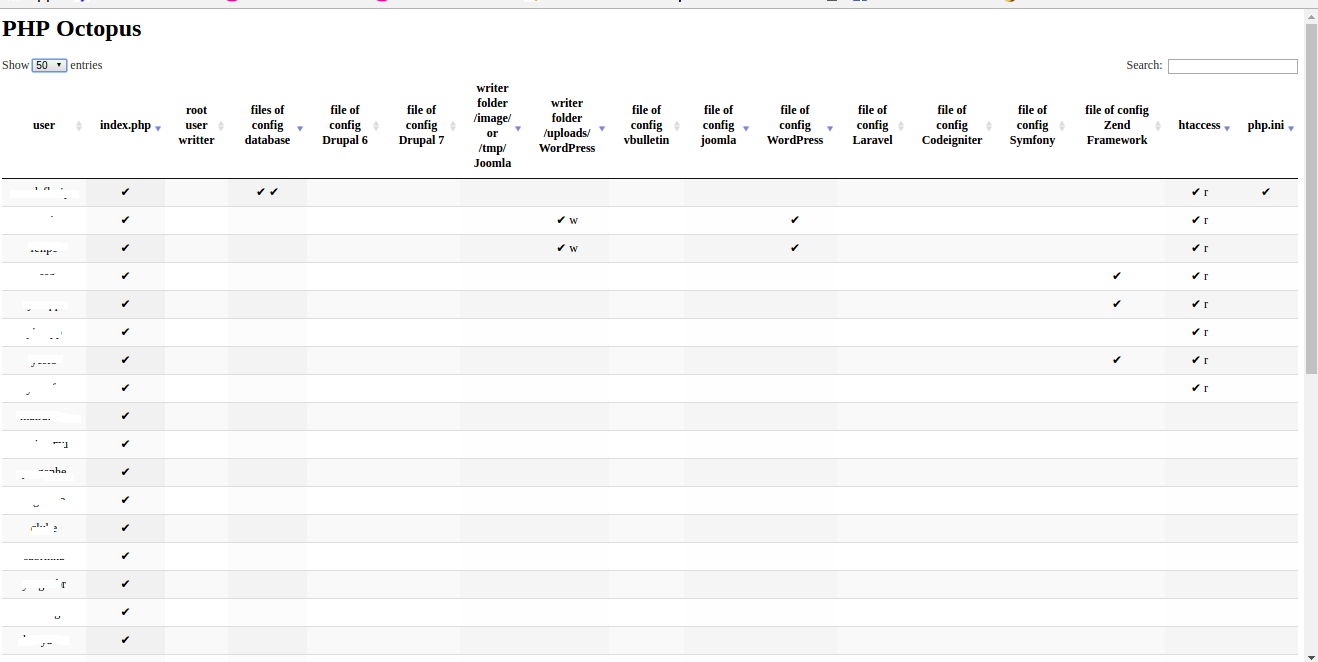
4 users, 11 found sensibles files:
Servidor 6:
1 user, 5 found sensibles files
Server 7:
21 users, 35 found sensibles files.
Clicking in check of column of configuration Zend file.



Mandou bem demais!!
Valeu mano =)
Sensacional brother ! A leitura foi de grande valor para mim ! abraço !
Pô, que bom mano, valeu o retorno.
=)
So por curiosidade, tds servers na mesma hospedagem ou em serviços diferentes?
Serviços diferentes Ricardo.